Backtrack 3 and Intel's 3945ABG wireless card
Having seen so many people in #remote-exploit trying their best to get Backtrack 3 working with Intel's wireless chipsets, mainly the 3945ABG, I decided to write a quick-howto. Lets start by saying it's not quite easy. The default driver for Intel 3945 chipsets can do normal wireless stuff, but can't inject. The injection driver can't do normal wireless stuff. So you have to pick your tasks, and thus which driver to use, carefully.
In this brief guide I'll show you the quick way of getting over to the injection driver, finding a network in kismet and throwing wesside-ng at it to obtain the key. Then I'll show how to swap back over and connect to the network you've just pen-tested.
So, how do you know this guide is for you? A nice quick way is to do
CODE: Select all
lspci | grep 3945ABGCODE: Select all
02:00.0 Network controller: Intel Corporation PRO/Wireless 3945ABG Network Connection (rev 02)The first thing to note is that the default driver for this card is called `iwl3945`. Using an `iwconfig` will get you something like:
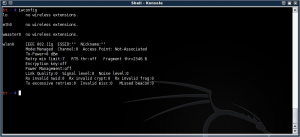
airmon-ng tells us:
CODE: Select all
Interface Chipset Driver
wlan0 iwl3945 - [phy0]CODE: Select all
/usr/local/sbin/airmon-ng: line 338: /sys/class/ieee80211/phy0/add_iface: Permission denied
mon0: ERROR while getting interface flags: No such deviceCODE: Select all
# modprobe -r iwl3945
# modprobe ipwraw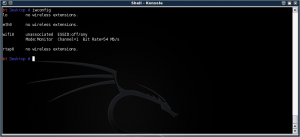
This wifi0 device can go into monitor mode:
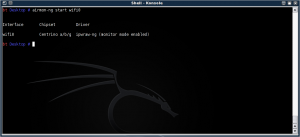
Now to find your network to pen-test (and of course, only do this on hardware you own. In this case we're going to use the BT Home Hub we have here).
First edit /usr/local/etc/kismet.conf in you fave editor. We're only going to change a single line, so no need to load anything fancy (I myself use nano, but use what you'd like)
Scroll down to the "source=" line. You'll want to alter the source line to read something like:
CODE: Select all
source=iwl3945,wifi0,Intel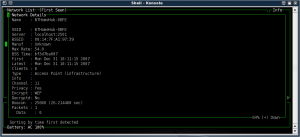
Note down the MAC address of the router, exit kismet.
Now the fun part. wesside-ng takes the tedious work out of getting all the IV packets and running aircrack-ng on them to get the key. To use wesside-ng:
CODE: Select all
wesside-ng -i wifi0 -v {BSSID}Here's wesside-ng after successful authentication:
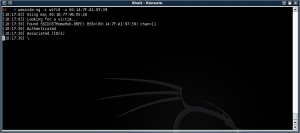
Here we're cracking the key:
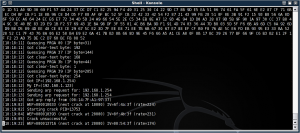
Tada, it found the test key, E723F7D5E8 (Yes, it's a 64-bit key for speed and testing).
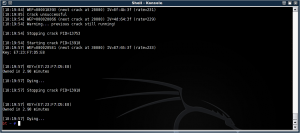
Now we need to prove this is correct. Reverse the drivers:
CODE: Select all
# modprobe -r ipwraw
# modprobe iwl3945There we go, success:
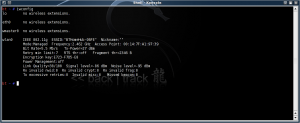
I hope this helps those who are stuck getting the Intel card to inject.
NeoThermic
Posted by NeoThermic on 31st December 2007 6:42pm »» 0 Comments »» Trackback this post »» Permalink